Editorial note
Writing in the first person is usually shunned in
technical writing, but the textbook _Network Security_ by Kaufman, Perlman and
Speciner makes the topic much more enjoyable by telling jokes and personal
anecdotes. This paper similarly conveys
meaning and shares real experiences in a friendly and informal atmosphere.
I. The 3 main elements
Authentication of people (users, humans) has been done
for centuries with passwords, tokens, secret handshakes, etc. The 3 main elements are
1. What
you know
2. What
you have
3. What
you are
II. What You Know
That is something that you have memorized: a password or
PIN. Or secret/private information such
as mother's maiden name, nickname, club password.
There are many problems with memorized phrases
·
People tend to choose weak or easy to remember
passwords
·
Passwords are easily compromised by just one
utterance or observation
·
Passwords are often stolen from users by spying
(shoulder-surfing, keystroke logging) or attacking weaknesses at the
authentication server (stored in insecure files)
Sadly, many systems encourage people to use weak
passwords. A recent example: I just
received a replacement credit card for one that expired (which is a rather weak
security system too: credit card numbers are easily stolen so the expiry,
holder's name or address is often used as a secondary identifier, but those are
also easily stolen or deduced. So credit
card companies now print an additional number on the back of the card that is
not embossed nor on the magnetic strip.
But of what value is that measure once the additional number is
compromised, such as a "phishing" fake internet site?) I was asked to create a 4 digit PIN, but it
only accepted 01-12 for the first 2 digits since they not only recommended that
I use someone's birthday as the pin, the entry system ENFORCED it! I was then transferred to a human to enter my
PIN, a human "white spot"!
I have resorted to circumventing the NJIT mandatory
password-changing system because I forgot my new "clever" password
several times now.
The NJIT system
·
Forces the user to set a new password after a
certain number of days
·
An ordinary user cannot set the password again
for a few days (although an administrator may always set the password again if
it's forgotten
·
Disallows reusing the 3 most previous passwords
Since I can't remember such temporary things, I'm forced
to choose weak passwords, or write them down.
III. What You Have
A photo ID is well understood by people, but it's not
machine-readable. Machine readable or
useable ID is usually an index into a database for the rest of the information,
such as an employee number or credit card number. That is made machine readable by
1. Barcode
2. Magnetic
stripe
3. Rfid
4. SecurId
5. SmartCards
A.
Bar Codes

Ordinary barcodes are good because they're easy to print
and machine-readable. Barcodes are on
nearly all store products because it costs nothing additional to print on the
label/container and it allows unambiguous identification of the item for
checkout (which is fast thanks to laser scanners and accurate thanks to
self-checking codes used in creating the barcode). Barcodes are often generated as needed, such
as on lottery tickets so winning tickets are automatically identified. It's now common for people to print barcodes
at home. http://stamps.com lets you print postage yourself, and many
store web sites offer bar-coded coupons and promotions which are printed at
home and brought to the store for scanning with the purchase.
ID badges often use barcodes for the employee number
mostly for the convenience of not needing to type it into a timeclock or door
lock. When I visited an office at the
World Trade Center, a digital camera at the security desk took my photo and
printed it on a one-time-use ID card with a barcode that activated the required
turnstiles and doors for me to get to my destination.
Ordinary barcodes are vulnerable to photocopying! The Pathmark supermarket allows me to scan my
own items at the “express" checkouts (albeit with camera and human
supervision), but I may not scan my own coupons: they must be handed to the
attendant because too many people were photocopying coupons or vouchers where
copies are not valid.
Infrared barcodes is the countermeasure to
photocopying. The equipment for reading
IR barcodes is identical to the visible light scanners; they simply use IR
light emitters and sensors. The obstacle
to deployment is the need for special paper or an opaque barrier over the
regular barcode. That way the stripe
looks like a totally black band under visible light but I-R differentiates the
stripes from the background.
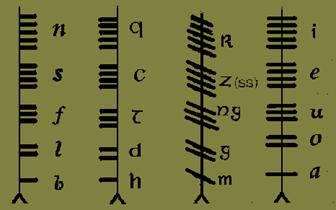
A slight tangent: barcodes are not a new invention! Here's a 5th century Irish barcode. This is a "ogham line" showing all
25 "letters" of the Ogham alphabet:
![]()
This relates to the security because it's a method of
secret writing! Long ago, watermarks and
secret writing were used to qualify documents, or secretly mark people as
troublemakers. Barcodes and
machine-readable codes might be used in similar ways to hide messages from the
bearer.
B.
Magnetic
stripe
The magnetic stripe is ubiquitous since it's inexpensive
and has totally displaced punched cards.
It's trusted for fare cards, credit cards, ID cards, etc. But it's vulnerable to erasure (by magnets),
alteration, forgery and duplication.
C.
RFID
RFID (Radio Frequency identification) is a contactless
way to read an ID from a tag. Sensormatic's anti-theft tags are the most well
known. The US Military is using RFID to
track inventory since it allows reading information from boxes deep within a
palette (no more labels falling off or being too dirty to read). Stores such as WalMart are aggressively
pursuing RFID but the cost is still too high, keeping barcodes the primary
method for tracking items.
Contactless ID cards are popular because they don't have
to be worn visibly and the readers have no moving or exposed parts. But there are privacy concerns because there
is no off switch or notification of activation.
Microchipping animals with a low range RFID ID is now required by the
European Union for pets traveling across boarders.
According to http://www.defra.gov.uk/animalh/quarantine/factsheet/euvetfactsheet2.htm
|
Animal health and welfare The Pet Travel Scheme (PETS) - Advice to UK veterinary
surgeons in GB: ·
European Regulation 998/2003 takes effect on 3
July 2004. It sets out the rules for pet animals travelling between European
Union (EU) countries and into the EU from other countries. ·
Microchip identification: We recommend that the
microchip conforms to ISO Standard 11784 or Annex A to ISO Standard 11785. If
it doesn’t, it may be impossible to read it when the animal is checked in
another PETS country. The owner is then required to provide a microchip
reader to enable it to be read. ·
To travel from the UK to another EU country, an
animal must, in this order, be microchipped, vaccinated against rabies and
issued with an EU pet passport. |
See also: http://www.animaldata.com/es/about.htm
In many countries (e.g. Australia, United Kingdom,
Norway, Sweden), microchip identification and registration is mandatory for
international pet travel purposes.
http://www.emmitsburg.net/vet/article_archives/general/microchip.htm
http://www.saveourstrays.com/chips.htm
http://www.moggies.co.uk/stories/pports_rules.html
D.
friendly
RFID: The Active Badge System
Many of the concepts used for electronic badge systems
have been embraced for beneficial uses by the UbiComp (Ubiquitious/Pervasive
Computer) movement. UbiComp is more than
just the evolution of the man/machine interface; it is teaching computers to
work in a more anticipatory and less intrusive manner. Instead of waiting for a command to turn on
the lights, a "smart room" senses not just that a person is in the
room but WHO is in the room and set things to their preferences. As people enter the room, the room atmosphere
automatically responds, trying its best to anticipate their needs and desires.
Andy Hopper et al. were the first to explore contactless
ID cards (using IR, not RFID) to provide the person's location in real
time. This ubiquitous computing
experiment explored desirable uses such as finding co-workers within the office
and phone calls automatically following you.
Some areas were intentionally NOT monitored and there were ways to turn
off the badge to respect privacy.
Another example from Professor Quentin Jones' UbiComp
class: a health club used such a system for the background music. As people entered the club, they used their
ID cards to activate the door. The music
in the workout room changed according to the people in the room to meet their
mutual needs. Each person has a music
profile that they set and may alter as desired.
People tend to understand the difference between place
and space and behave accordingly. The
same church room may hold funerals and weddings yet people behave differently
for the circumstances. Teaching that to
machines has proven difficult. Consider
cellular phones. They cannot currently
sense when it is inappropriate to ring out loud. Some places have resorted to jamming cellular
phones entirely because there's no universal method for silencing them. Asking patrons to turn off their phones (or
set them for silent alerts) does not generate sufficient compliance. Perhaps when all cellular phones have a standard
wireless interface such as Bluetooth they will also honor standard commands
such as "silent mode" from a transmitter in the room, which is
activated when appropriate.
What security folks call tokens, UbiComp calls phidgets or tangible bits [lutz03].
Instead of walking up to a keyboard or sensor, people handle physical
objects that are sensed and tracked by the computer. "Digital Chopsticks" allow people
to point to each other's display (hand held PDA, laptop, etc), pick up and move
data as if it were physically picked up by the chopsticks. This is much more intuitive than clicking and
dragging things to icons which must first be linked to the other person.
At Linux Expo 2003, IBM demonstrated the security
features integrated into their ThinkPad laptops, making it harder for thieves
to simply take the data from the hard drive or use the stolen computer. The authentication allowed adding PCMCIA
cards for SmartCards, fingerprint scanning and a proximity sensor. Like an active badge, the wearer has an RFID
badge that participates in logging into the system (remember the basics: it's
not just WHAT YOU HAVE but WHAT YOU KNOW: an ID or PIN is still
essential lest someone steal the card and impersonate you). If the wearer is
too far from the system (the distance is adjustable) then the screen blanks
(for privacy) and the input devices (keyboard, mouse, touch screen, etc) all
lock until the person returns.
A friend told the story of the time he interviewed at
the NSA. Whenever he entered a room,
"RED BADGE" was announced (apparently meaning "visitor with no
security clearance"). The sound of
many cabinets and drawers being closed and locked instantly followed. Had visitors been issued an "active
badge", then only systems within range would automatically blank their
screens and systems further away would automatically warn the user that the
system will blank soon if the guest walks too close.
Combine these scenarios: what if my photo were taken
upon entering the building (such as the security system the World Trade Center
used) when I was issued a temporary/visitor's active badge. If the facial recognition (or other) system
later determined that I was a possible bad-guy, then my location in the
building would be instantly known by the badge-sensors.
E.
Delegation:
it's not who you are, it's who you're working for
In the identification, authentication, authorization
triad, tokens are an authorization device.
A token is granted after passing authentication and grants the bearer
certain permissions. When visiting an
office, the front desk authenticates that I have business there and grants me a
visitor's pass. That is my token to
proceed. Tokens may be virtual too: at
an internet cafe, I may be given a temporary password to use the computer. Some tokens are not linked to a specific
person and may be handed to others and the permission or privileges are
transferred to that person. This is
often desirable to allow temporary access to some facility that is normally not
accessible (such as the key to the locked bathroom). Tokens (or tickets) are a vital link between
authentication and authorization as in voting systems.
F.
Voting systems
Voting systems are a unique environment. The person must be identified and
authenticated as a registered voter, but the voting must be anonymous,
irrefutable, unalterable and auditable.
And each voter may cast only one vote.
The current system of signing the logbook and getting a ticket to
proceed to the voting machine is a deceptively simple and straightforward
method of achieving all the identification and authorization requirements. Identification and authentication occurs when
I present my photo ID at the registration table and sign the logbook. My signature may be compared to my voter
registration card for further authentication, but it also leaves evidence that
I was there in person (nonrepudiation), and prevents me from voting twice since
I can sign in only once. I am then
handed a ticket that authorizes me to cast one vote at the voting machine. The ticket is an intermediate step that
separates authentication from authorization and allows me to vote
anonymously. It an elegant system
because no step can be removed.
The Florida presidential election demonstrated serious
flaws in low-tech ballot systems, so new solutions are urgently sought. All electronic systems are being rejected due
to lack of safeguards, public review and lack of a verifiable audit trail. http://www.accupoll.com/ is a good example of a solution that
offers an unalterable paper audit trail.
The accompanying CD contains many comp.risks digests
[RISKS]. Of particular interest are the
news stories this week from California, where the Diebold electronic voting
machines were decertified and not valid for elections due to lack of any
meaningful audit trail and an inexplicably high error rate, as well as lack of
trust in the programming used within the machines.
G.
Weaknesses
All these systems have weaknesses:
·
Passwords/pins are guessed or shoulder-surfed
·
Barcodes can be photocopied
·
Magnetic cards can be “skimmed” http://www.snopes.com/crime/warnings/atmcamera.asp
describes a clever ATM device that use WiFi to transmit the card data and even
a camera to see the PIN entered on the keypad.

H.
Surreptitious
identification
Despite the advantages an active badge system provides
when it benefits the user, there are nefarious uses for tracking people,
vehicles or items, particularly when the person is not aware of the
surveillance or cannot choose to decline participation.
·
The Digital Convergence CueCat barcode scanner
was given away for free by Radio Shack, Forbes magazine and others. The alleged intention was for people to scan
the barcode from advertising or products and get to the related web page. The company is out of business because of a
flawed business model: they spied on everyone using the barcode scanners to
create a database of interests and never disclosed that intention to the
end-user. Each scanner has a unique ID
number and encrypted the scanned barcode to force the user to send that data to
Digital Convergence's server to map the barcode number into a related URL. It is not known if everyone received the same
reply, or if your profile steered you to different web sites (i.e.: people with
profiles indicating wealth would be directed to web sites featuring the most
expensive models). Happily, the barcode
scanners are now ours to keep and there are many web sites showing how to
defeat the serial number and there's even a contest to write the shortest
program to decrypt the output so it's useful by itself.
·
Wireless cards can be read without permission or
action on the user's part. The German
store "Metro" placed RFID in the customer loyalty cards but failed to
disclose anything about their existence or intended use. Since they can be read from 10 feet away,
sensors at the door could take attendance even if you don't buy anything. Sensors around the store could monitor where
you tend to dwell, regardless if you actually buy anything. http://www.spychips.com/German%20RFID%20Scandal.htm
documents how it was revealed and the store's immediate withdrawal of the
program.
·
Embedded serial numbers are in computer
peripherals, thus enabling "spyware" to track you from the computer
parts, not just the system as a whole.
But such information is also useful for tracking one's own inventory,
particularly for large companies.
·
Walmart was exploring the merits of RFID tags
replacing barcodes on all items. They're in a position to force all their
suppliers to use RFID or not get stocked in the store. People are deeply concerned about their
privacy, particularly since the tags may be so deeply embedded in a product
that it cannot be removed or deactivated.
Happily, the incentive is on hold because RFID tags are still too
expensive (despite many clever fabrication techniques such as using printing
methods for making the antenna instead of foil or wire). And there are countermeasures for RFID: place
the item in a properly shielded bag.
·
When facial recognition systems mature, you can
be identified without your knowledge or consent by a remote camera. Wearing dark glasses or large hats helps.
I.
White spot
elimination
A weakness of many systems is the "white
spot": the point in the system where the information is not protected and
is vulnerable to spying. Simple passwords are vulnerable to being observed and
re-used (playback).
A One-time pad prevents that, but few people can
memorize anything random enough to be secure.
Token devices such as SecurID allow the user to enter the response using
any numeric input device (keypad, touch-tone phone) via an insecure channel
because the value is valid for a short time, cannot be reused, and the sequence
cannot be guessed. Pirate ATMs and
hardware that records all of a PC's keyboard strokes are now common, but
properly designed security devices encrypt the data right at the source. Bank PIN pads don't transmit the data in the
clear but are encrypted right at the keypad (the keypad controller needs to be
initialized with a session key, it's not merely read like a standard keyboard).
Similarly, secure input devices such as hand scanners and fingerprint readers
must communicate securely to prevent replay attacks at the communication link. SmartCards have no white spot (except for the
initial programming and manufacturing phase) so they may actively participate
in standardized secure communications [rfc1824] [rfc1875] [rfc3193] [rfc3457]
J.
SecurId
RSA SecurID is a token: a device that looks like a
calculator or digital watch and displays a time varying number. When combined with an ID or PIN, it forms a
one time password. The server has a
matching algorithm to verify the user and corrects for clock drift since the
token works stand-alone. I think of it
as a secure hash of time and password.
Advantages of this system
·
No special equipment is required to use it: just
a keyboard for entering the magic number
·
It thwarts replay attacks: even if the reply is
captured it is valid only once and for only a short time (Kerberos uses a
similar argument for why ticket theft is not such a problem).
The disadvantage
·
The server must be accessible in real-time for
validation
·
One token per person is required, which is
expensive
K.
smartcards
Smartcards contain a processor and nonvolatile memory so
they perform dynamic data processing capabilities in addition to data
storage. The chip is so small that it's
often embedded in something larger to make it easy to carry, such as credit
card or key shape. Unlike memory cards,
it actively participates in the secure conversation from the host, so even
eavesdropping cannot clone the card or reply the transaction.
I am an advocate of SmartCards. See [jonas03a] (on the accompanying CD) for
an introduction to SmartCards presented to Professor Jones' class. In [jonas03]
(on the accompanying CD) I propose a SmartCard based system for personal ID
addressing privacy issues described in [HILTZ03]. Instead of granting access to all information
in the card, information is tagged with access levels: PRIVATE or PUBLIC. The cardholder must actively participate in
retrieving PRIVATE data to grant permission (although an escrow mechanism is
possible for emergencies such as accessing medical history during an
emergency). I also recommend an audit
trail in the SmartCard itself, assuring a checks-and-balances system so the
card bearer may review who accessed the card, when, and what information was
requested. Despite SmartCards being
programmable and alterable, the data is trusted because it's signed by a
trusted third party similar to a certificate.
An X.509 certificate easily fits into a SmartCard's NVRAM with room left
over for much more user data.
American Express' Blue cards are SmartCards. They offer free readers for home use on your
PC (USB or serial interface) so properly programmed web sites access the
SmartCard directly to prove that the person at the keyboard is the card bearer
since the card MUST BE PHYSICALLY INSERTED into the reader. Sadly, they withdrew support for
"Private Payments" (a one-time-use account number was generated using
the card in the card reader, thus allowing one transaction but preventing abuse
of the account as could happen by disclosing the permanent account number).
During a class discussion of key management, Rajat
suggested keeping all one's passwords and account information in one file and
encrypting that, so only that key needs to be memorized. It's the electronic equivalent of placing all
your passwords and secrets in a safe and only having to remember the safe
combination. Apparently the American
Express SmartCard has that application already. According to http://www.americanexpress.com/igotblue
|
ID Keeper is the FREE Web tool only for Blue – that
stores your Web information right on your Smart Chip. With ID Keeper you can get to your favorite
sites, shop, and manage your finances with high speed and security. |
Target stores have already given up on their
virtual-coupon program. Since I, and
none of my friends have ever heard of the program, I fault their inability to
inform customers of such an innovative program!
Target issued SmartCard Visa credit cards with the store logo. The intention was for customers to shop
online and instead of printing bar-coded coupons (yes, a valid use of on-demand
barcode printing), a SmartCard reader on the PC stores the coupons on the
person's Target Visa
SmartCard so they were automatically applied to the
purchase when paid using that same card!
I am extremely discouraged by the shortsightedness of
American companies already withdrawing support from a SmartCard
infrastructure. It is a very worthy
technology in which European nations are heavily investing because they know
it'll reduce fraud and allow new features that will encourage acceptance and
consumer confidence. Had American
Express (which tries to differentiate itself from other credit cards by
specializing in traveler's needs) teamed up with New Jersey Transit and
installed SmartCard readers in the TVM (Ticket Vending Machine), then I'd
faithfully use my American Express card for all ticket purchases because
inserting the card would automatically identify my preferred language (English)
and my most likely purchase (round trip ticket Newark to Elizabeth). There would be no need to navigate 6-8 menus
every time to buy the same tickets that I usually buy. Even if I choose a different destination, the
menus would know to start in English and "choose a different
destination" would be the bottom choice with my usual choices above.
Referring back to IBM's secured ThinkPad laptops, there
are several security products for laptops that use SmartCards, either via a
PCMCIA reader, or self-contained in a USB key-fob. Vital parts of the file system depend on the
presence of the key, else the data on the hard disk is inaccessible.
Back to the SmartCard technology itself: the SmartCard
is a computational element of the protocol, not just a storage device. Think of all the diagrams with boxes and
arrows back and forth for getting a certificate, or answering a query to prove
one's identity. The SmartCard is the
piece of equipment participating in the protocol, so there's no white spot. Private keys remain secret to the SmartCard
because the code that uses it also resides on the chip. There's no way to get secret information out
of the chip. It's used to participate in
protocols, but never directly revealed.
When properly implemented, this makes SmartCards impossible to clone.
Satellite TV receivers use SmartCards for authenticating that the user is a valid
customer and authorizing what
channels they may receive. Unlike cable
systems where a reverse channel allows the cable operator to read the
converter's status, satellite receivers are totally passive. There is usually no link from the subscriber
back to the provider (except for services such as internet or phone service
which are intrinsically bi-directional).
The cards are now available on the black market for receiving
"free" cable TV due to a theft of the programming codes. The SmartCards were not cracked to achieve
the cloning.
Despite industry reluctance, SmartCards already deployed
·
In cellular phone SIM (Subscriber Identity
Module), the permanent ID is protected, but the phone list, user preferences,
calendar, etc are stored in it too.
·
Vending machines use prepaid "stored
value" cards (the laundry room in my apartment building too!)
·
American Express's "Blue" card has both
the magnetic strip and a SmartCard.
·
Military: ID smart-cards augment dogtags, used
for authentication and multi-level security access. The U.S. General Services Administration
[GSA] is fostering the use of SmartCards.
A survey of Federal Smart Card Projects [GSA04] seems to show acceptance
and successful deployment even for non-active personnel (such as Veteran
Administration Health Administration benefit cards).
SmartCards pose ethical, privacy and security concerns:
·
Does the cardholder have the right to examine all
the contents of the card?
·
Is each content provider required to disclose the
data, when and how it's used?
·
May we administer internal data similar to the
way web browsers have "cookie" control?
·
Will all smart card applications be bound by
rules for privacy, security and disclosure?
IV. Biometrics: proving what you are
People are remarkable for recognizing friends and noting
imposters. Teaching that to machines has
proven extremely difficult because they cannot correlate enough information
accurately. Recent techniques are:
1. Handprint
2. Fingerprint
3. facial
recognition
4. eye
scanning (retina or iris)
5. Voiceprint
6. Signature
A.
Biometric
timeclock

This clever device still requires your ID (note the
keypad for ID entry and slot for ID card) but uses your hand's unique geometry
as a secondary identifier. The database
continually updates your profile to allow for aging and follows the changes in
your hand over time. The reason for the
secondary identifier is to thwart "Buddy Punching" where the first
person to arrive punches in all their friends and the last person to leave punches
out all their friends, thus falsifying the hours actually spent on the
job. But it's more than just a time
clock: it can operate doors, and even display messages for the person clocking
in.
The IBM Kingston NY museum displayed their early
timeclocks. Photos showed huge
timeclocks with paymasters supervising each employee punch in and hearing the
bell ring ONCE to verify the punch was completed. (Some were huge drums inside
a locked box but rotated by a huge dial to the employee's "clock
number". The paper on the drum had one line per employee with the time
stamped left to right. That way only the
paymaster could access the paper and nobody could alter it). Trying to punch in someone else ment pointing
the dial to the other clock number and ringing the bell again which is easily
caught by a watching person.
Some places tried using the door-access card for
attendance on the premise that you have to walk in, but most doors allow exit
without swiping the card. The result is
recording only arrivals but not departures.
Manhattan offices tend to have turnstile-type entrances so everyone must
use their card to enter. But it's
natural for people to "piggyback" and enter a plain door once it's
opened.
Since timeclocks are rarely supervised anymore, other methods
are used to prevent friends from clocking in others. Some require the person's ID card for the
magnetic or optical stripe (common in supermarkets and stores), but combined
with biometrics such as handprint reduces abuses.
B.
Fingerprints
Fingerprint scanners integrated to laptops were
discussed in the active badge section above.
My cousin Lynda is a cardiologist.
Her office computer uses fingerprint scanning, as mandated by the
privacy and security policy of the insurance companies. But that fails to take into account an
occupational hazard: scrubbing for an operation is harsh enough that the
scanner does not recognize her fingerprint by the afternoon!
C.
Facial
recognition
A Google search for "face recognition
homeland" found 5,000 hits. The
good news is that many universities are getting funding for creating new,
reliable facial recognition systems and many bright people are finding creative
solutions. The bad news is that some
companies have already failed by rushing to implement facial recognition
systems in airports only to find that the technology is too premature for any
effective use at this time. Failures
included
·
Not recognizing known terrorists. Face angle and lighting seemed to create too
many differences for the system to compensate.
·
Taking too long to screen each person.
·
Presenting too many possible matches to the human
operator. 5 or fewer possible matches is
reasonable, hundreds is not.
In [SCHNE03] [CRYPTO] Bruce Schneier discusses real
world needs vs. the systems implemented and how they rarely match. Many companies reacted to 9/11 with security
measures, which are mostly ineffective, and a waste of time and money. He revisits the pillars of security by
evaluating real world systems for
1. What
assets are you trying to protect?
2. What
are the risks to those assets?
3. How
well does the security solution mitigate those risks?
4. What
other security problems does the security solution cause?
Applying that to a facial recognition system with 99.9%
accuracy (which no real system is yet to achieve) shows that it's mostly
ineffective because
·
It only detects known criminals for whom useable
photos are available
·
The false alarm rate is too high. Harassing innocent people takes time and uses
resources better used elsewhere.
Scanning 10 million people would result in 10,000 false positives. Scanning everyone at a football stadium would
create 75 false alarms per game and one real terrorist every 133 games.
What is the cost of a false negative: granting a known
terrorist entrance. Perhaps nothing:
there's no guarantee that he's there to do anything malicious. Perhaps
everything: if he's there for malicious purposes, but some secondary screening
is needed to determine that: is he carrying a weapon or something totally
inappropriate for the occasion? Sadly,
such screening failed on 9/11 since the terrorists did not use any weapons on
the "watchfor" list.
What is the cost of a false positive: detaining innocent
people. Besides hurt feelings, it could
lead to massive resistance to the system, particularly if patterns of
discrimination are reported. It also
consumes resources to process each person.
Some systems are "closed loop" and learn from
their mistakes. There are many cases of
people who are constantly harassed because their names are too close to
suspected or known criminals. Issuing
them a "It's not me!" ID card has a problem: the known criminals will
forge them for themselves! It's up to
the system and/or the operators to compensate for this (without introducing too
many loopholes) else the system will be mostly ignored as "advisory".
D.
The future
as we saw it
Science fiction movies portray alternate realities where
technology allows constant surveillance of everybody.
The science fiction movies "Gattaca" and
"Minority Report" are similar in their depiction of a near future
where everybody is under constant surveillance.
In both movies, the main character/hero/protagonist circumvents the
security system to prevail. Happily,
their goals were for the common good, as opposed to glorified villains/criminals.
In Minority Report, retina scanning is the primary means
of identification to the exclusion of all else.
The hero gains a new identity with an eye transplant, but saves his old
eyes to regain his previous authorization.
He was falsely accused of a murder he didn't commit while the creator of
the crime detection system commits many murders and remains undetected because
he purposely created loopholes in the system so he was above observation,
review or suspicion. The lessons are
very valuable for today's security:
·
ALWAYS use multiple measurements to verify
identity
·
Over-reliance on one technology or implementation
leads to a monoculture where one attack will always succeed [thus all the
worms/viruses for Microsoft products]
·
Security via obscurity ALWAYS hides flaws [thus
the public peer reviews of cryptographic systems and open-source operating
systems]
·
Everyone in the system is accountable for their
actions [from the sleeping security guards to the director creating policy
loopholes]
·
No person, place or thing is above
accountability, audit or inspection
·
A checks-and-balances system is essential for all
levels and scopes: from the reliability of individual components to the overall
system preserving people's rights [an example from recent news: the U.S. is
accused of denying the prisoners detained at Cuba's Guantanamo base of
"due process". This
contradicts our intention of allegedly defending the Iraqi’s rights to a
democratic & representative government when we're violating our own democratic
process].
In the movie Gattaca, the DNA scientists are above
reproach, so when a baby is born the DNA analysis is used to predict the
child's anticipated aptitude and health.
Despite laws to the contrary, a caste system results with
"valid" people getting the desirable jobs solely on good DNA
expectations and "invalid" people as janitors for life. There is no appeal process or method for
re-evaluation based on what you actually achieve. The hero had the aptitude and physical
endurance for space missions but was forced to cheat and circumvent the unfair
tests to reach his full potential.
The authentication systems were extremely thorough by
testing anything containing DNA: blood, saliva, urine, hair, skin. But there were secondary matches on face
photo, height, need for corrective vision, any handicaps or abnormalities.
His methods were clever technical and social
engineering:
·
Fake fingerprint and blood-bladder beneath it to
pass the daily fingerprint and blood tests just to enter the building
·
A bag inside his pants for the random yet
incessant urine tests so even the donor's urine was the correct temperature
·
Constantly cleaning his work area and leaving
skin and hair from his assumed identity.
As the murder investigation increases, the screening
tests heighten due to the diligence of the detective:
·
ONE of the hero's hairs was too close to the
murder scene. It was collected and
identified, but linked to his previous identity. So the game is for him to keep his new and
previous identities totally separate despite all the opportunities for even a
single hair or saliva to correlate his previous identity and his current
location.
·
When blood is drawn under observation from a
vein, he can't fake that, so he creates a diversion and switches sample vials.
·
At a police roadblock, he refuses the throat swab
(which he cannot fake) with a blood test from his fake-finger-bladder.
·
When the night club is raided, he has no choice
but to beat up a guard and flee. Low
tech but effective!
·
When he's not prepared for one last urine test,
the technician passes him anyway because his son too was deemed
"invalid" so he was a silent partner all along due to his hidden
agenda.
Both movies exemplify how people circumvent even the
most technically advanced security systems, particularly if there are
sympathizers due to flawed policies.
In the TV series Space 1999, the Comlink was a
videophone, communicator, door key, and multifunction terminal. That classifies it a token type device. One can hope that it recognized the user in
some way so it does not grant full access to anyone who picks it up! Cellular phones are now close to that: they
have high resolution color screens, cameras, keyboards and because their SIMM
SmartCard is considered a secure form of identification, it may soon operate
vending machines and act as a key.
Unless a PIN or password is required, it's hard to prove who is using it!
E.
Other
Biometrics
Phrenology is the study of the conformation of the skull
based on the belief that it is indicative of mental faculties and
character. Phrenology is an abandoned
practice because it was mostly attempting a "scientific" basis for
prejudice. It's been debunked as a
predictor of anything useful, along with palm reading, horoscopes, handwriting
analysis, etc. There's always the danger
that biometrics will be misapplied or abused for discriminatory purposed. For instance, in the movie
"Gattaca", DNA predictions were used to classify people into a caste
system regardless of the merit or accuracy of the predictions.
What brings phrenology to mind is the recent popularity
of head massagers such as "The Tingler" and the HeeBeeGeeBee(TM)
vibrating head massager where a spider-like device of many wires massages the
scalp reminiscent of the many probes used for measuring the skull shape. Unless significant differences in skull
shapes can be meaningfully observed then it's hardly a useful primary or even
secondary identifier.
Forensic medicine may offer insights into useful
biometrics since that explores legally admissible identification based on
permanent and unique body characteristics such as dental records.
F.
Profiling
vs. Intuition
Even if computers were given more input such as lie
detectors (polygraph, voice stress analyzer), they lack human intuition. Several terrorists were caught by immigration
and boarder officers by observing that they were "twitchy" or
overcompensating by "trying to act cool".
Sadly, humans have biases that sometimes interfere with
proper judgement, such as racial profiling.
G.
But I tell
you, my friend, it's not where you are, but your reason for being there. --
Utah Philips [Utah]
Citing [SCHN03]
|
Identification, authentication and authorization. The three concepts are closely related, but
in a security system it's critical that we tell them apart. ·
Identification: Who are you? ·
Authentication: Prove it. ·
Authorization: Here is what you are allowed to
do |
Most of this paper deals with the first 2 items: proving
I'm me. But mapping that to permissions
is a different mechanism. Visitor's
passes are a form of consumable ticket: they expire based on time, or I hand it
back on the way out. Even a plain paper
pass may be stamped "valid only for floor 9 on May 5th". Logging into
computer grants me access to my files and shared facilities. It's considered
trespassing to access facilities or information that are not part of that
permission.
H.
You got to
be very careful if you don't know where you're going, because you might not get
there. -- Yogi Berra
The Homeland Security Advisory System [HOMEL] is sadly a
negative example of how to implement a security system. Despite all the publicity for
red/orange/amber alert, there are no clear procedures for people to follow or
clearly stated goals or intentions.
"Vague alert" jokes are too true: the color code is mostly
meaningless to people because there's no manual "what it means to me and
what am I to do". There is little
confidence in the system determining the color-code because it's now "the
boy who cried wolf". Tremendous
panic and anxiety has been caused by false alerts from unreliable sources. The main tenant of asymmetric warfare is
causing FUD (Fear, Uncertainty and Doubt) and economic damage at minimal cost.
It seems the Homeland Security levels are helping the terrorists by giving a
stamp of legitimacy by publicizing groundless threats from fakes.
I.
implementing
faulty systems in a rush
I remember several unpleasant experiences where the
person charged with implementing security was not solving the problem
completely, or failed to heed others' experience.
The first problem was dictating policy to others instead
of appealing to people's sense of duty or responsibility to participate. People resent rules but tend to respond
favorably if treated with respect. It
costs nothing to get people to collaborate.
Respectfully explaining the mutual effort required and motivating people
to do their part ought to work wonders.
Sadly, I am yet to meet any such security expert.
One example: paper shredders appeared around the office
without explanation. I asked if I had
missed a memo explaining their use for other sites had clear systems for
classifying documents as "internal use only", "company
confidential", "secret" and such, so I expected that only
confidential or higher required shredding. That question nearly cost me my job,
for I had embarrassed the security officer who had not gotten around to stating
any policy for their use.
Another example: at one work site, there were security
guards at the front entrance checking for ID cards, so none of the inner doors
were locked. Then ID card activated
locks were added to the top floor doors.
Since the doors can be held open, people tended to “piggyback" and
enter if a colleague had opened the door first.
There was no motivation to "key in" to an already open door,
particularly since there was no need to "key out". The system only logged people entering the
top floor but not exiting. I tend to always key-in because on several occasions
I used the security system's entry log to disprove false accusations that I was
late to work or not on site for a particular day. My diligence is due to the protection the
system offers me from such accusations ("exempt" employees are not
monitored by a timeclock system). If not for such personal motivation, it is
unlikely I would always comply.
Manhattan offices have a simple solution to the entry
problem: they use turnstiles so everyone must use their ID card to enter every
time (but it's NOT needed to exit).
V. Lessons learned
·
Correlate multiple factors, don't reply on just
one technology or input.
·
Using only one technology or implementation leads
to a monoculture where one attack will always succeed.
·
Security via obscurity only hides flaws.
·
Everybody in the system is responsible for their
participation. Only one weak link is
needed for total failure.
·
No person, place or thing is above suspicion, so
checks and balances are required at all levels.
VI. Closing remarks
Security is an evolving field with new expectations and
new technologies that may help solve them.
Since 9/11, there's an increased fervor for security, but until goals
are clarified, there is no silver bullet.
Appendix A
RFID manufacturers
and news
http://www.alientechnology.com
Alien Technology is a leading supplier of radio
frequency identification (RFID) hardware that enables consumer packaged goods
companies, retailers and other industries to improve their operating efficiency
throughout their supply chains. ...
Matrics provides EPC compliant RFID systems for retail,
CPG, defense, transportation and other vertical markets. ...
IDTechEx is the world's leading independent analyst on the
development and application of RFID smart labels and smart packaging
technologies.
http://electronics.howstuffworks.com/smart-label.htm
a pleasant introduction to RFID
http://news.com.com/2100-7337-5104493.html?tag=nl
Wal-Mart puts big bucks into tracking tech
Last modified: November 7, 2003, 2:41 PM PST
By Alorie Gilbert Staff Writer, CNET News.com
Wal-Mart plans to spend $3 billion over the next several
years on a new inventory tracking technology that uses radio frequency signals
to keep tabs on merchandise, sources familiar with the project said.
The system is based on a technology known as radio
frequency identification (RFID), a new breed of computer network designed to
track the location of everyday objects such as razors and shoes by embedding
them with special microchips. Wal-Mart
has enlisted its top 100 merchandise suppliers to participate in the high-profile
project, one of the first and largest of its kind in the retail industry.
http://news.com.com/2100-1022-1013767.html?tag=nl
Wal-Mart to throw its weight behind RFID
Last modified: June 5, 2003, 2:41 PM PDT
By Richard Shim Staff Writer, CNET News.com
Inventory management technology that uses wireless
signals to track products from the factory to store shelves is set to win a
major new ally next week: Wal-Mart.
The retail giant is expected to throw its weight behind
RFID (radio frequency identification) technology at the Retail Systems 2003
industry conference in Chicago on Tuesday. Sources familiar with the company's
plans said executives will make a presentation encouraging its top 100 suppliers
to start using wireless inventory tracking equipment--chips affixed to
products, and scanners in warehouses--by 2005.
http://www.silicon.com/networks/lans/0,39024663,39118760,00.htm
Supermarket cans RFID trials in Germany
March 01 2004 by Jo Best
Consumers not best pleased by tracking loyalty cards
The latest trial of RFID in high street shops at the
German supermarket chain Metro has met with protests that have seen the
retailer backtrack after consumers objected to the tracking tags turning up in
their loyalty cards as well as consumer goods like Gillette razors.
Despite a promise by Metro that the stores will stop
using RFID, civil liberties and privacy advocates protested outside the shop on
Saturday.
An in-store kiosk was meant to disable the tags before
shoppers left the supermarket, but it was found to be ineffective, meaning
shoppers and their purchases could theoretically be tracked outside a store as
well as inside.
Metro the fifth largest retailer in the world and the
biggest in Germany - has also offered to replace the cards of any concerned
shoppers with cards sporting bar codes instead.
Despite making no secret of its plans to the trade
press, the Extra Future store in Rheinberg didn't reveal its plans to use the
technology in 10,000 cards to its shoppers and the RFID tag was only discovered
when one of the cards was taken apart by an activist.
While the store has decided to recall its loyalty cards,
plans for an RFID-enabled inventory system across 250 stores and 100 suppliers
will continue, said the retailer.
Metro isn't the first retailer to shelve plans for an
RFID rollout after an unfavorable reaction from the public. American favorite
Wal-Mart announced last year that it would be putting plans for RFID 'smart
shelves' on ice, but like its German counterpart, would be using the tracking
technology in the supply chain.
http://www.silicon.com/networks/mobile/0,39024665,10005065,00.htm
Wal-Mart cans 'smart-shelf' store trials
July 09 2003 by Alorie Gilbert and Richard Shim
Bar-code replacement smart tags will now only be used in
its warehouses
Wal-Mart has unexpectedly cancelled testing for an
experimental 'smart-shelf' in its US stores that would have used the
controversial radio frequency identification (RFID) product tracking tags.
The trial with Gillette was due to begin at a store in
Boston last month but Wal-Mart spokesman Tom Williams said this has now been
ditched.
He said: "The shelf was never completely installed.
We didn't want it. Any materials that
were there were removed. We never had products with chips in them."
RFID technology uses microchips to wirelessly transmit
product serial numbers to a scanner without the need for human intervention and
is seen as an eventual successor to bar-code inventory tracking systems,
promising to cut distribution costs for manufacturers.
Wal-Mart's proposed smart-shelf system was designed to
pick up data transmitted from microchips embedded in Gillette product
packaging, alerting store managers via computer when stock is running low on
the shelf or when items may have been stolen - two informative and powerful
measurements in the retail business.
The trial would have been the most aggressive step yet
by a retailer to push RFID from warehouses into stores. Backers of the
technology eventually see billions of packaged goods tracked remotely using
RFID sensors through in-store systems that might one day help prevent
shoplifting and speed shoppers through automated checkout lines.
Those ambitious plans now are likely to take a backseat
to proposals to upgrade warehouse operations with RFID technology, which will
require fewer chips and less computational power.
Wal-Mart, the world's largest retail chain with 4,700
stores around the globe, said last month that it is urging its top 100
suppliers to attach RFID chips to cases and pallets of products that they ship
to Wal-Mart warehouses.
A Gillette representative declined to comment on Wal
Mart's decision to pull the plug on the wired shelf but said the company
remains focused on helping UK supermarket chain Tesco and German retail
conglomerate Metro with similar trials in Europe.
The smart-shelf trial by Wal-Mart was viewed as a
potentially aggressive endorsement of an in-store application because of the
company's ability to influence its suppliers and push the adoption of new
technologies - something it helped to do with bar-code scanning technology in
the 1980s. The unexpected cancellation of the test is letting some of the steam
out of the market, but that may be a good thing, according to one analyst.
Jeff Woods, analyst with research firm Gartner, said:
"The RFID industry has been floundering in a sea of science projects,
which is what these trials have been to date. This is one of the most overhyped
technologies out there, and this can be viewed as a precursor to the bubble
bursting for RFID."
Privacy advocates have aired concerns about the
technology and whether retailers and manufacturers would be able to monitor
products after consumers purchased them.
But in May, several RFID chip manufacturers pledged to
incorporate a "kill switch" that would be disabled at checkouts into
their chips in a move to relieve consumer fears of the technology.
Economics may have played a role in Wal-Mart's decision
to shelve its in-store RFID test. RFID chips are still too expensive for
wide-scale use with consumer merchandise, according to Gillette spokesman Paul
Fox.
While today's price of around 10 cents a chip is cheap
enough to fuel initial trials the cost of the chips have to fall to a fraction
of a penny if they are to become ubiquitous in stores, which could take up to
15 years, he said.
Alorie Gilbert and Richard Shim write for CNET News.com
[several web sites report on RFID abuses and invasion of
privacy]
The main web site for CASPIAN (Consumers Against
Supermarket Privacy Invasion)
RFID chips, tiny tracking devices the size of a grain of
dust, can be used to secretly identify you and the things you're carrying--
right through your clothes, wallet, backpack, or purse.
Business Week: "Industry is finally getting the
message:
RFID is fine for pallets of goods in a warehouse, but
not for people."
http://www.spychips.com/metro/scandal-payback.html
An x-ray of the card shows the internal antenna, and
discusses the lecture about RFID privacy where the store knowingly lied and
misled customers about the technology and the store's intentions.
http://www.wired.com/news/business/0,1367,62468,00.html?tw=wn_tophead_5
RSA Security has developed a countermeasure to block
scanning of radio-frequency ID tags, responding to privacy concerns about the
tiny devices that would allow retailers and manufacturers to track the
whereabouts of their goods within a store and beyond.
At a computer security conference in San Francisco,
RSA Security gave out medicine bottles filled with
jellybeans. Embedded in the bottle's
label was an RFID tag similar to the kind that retailers may use to track their
products. An RFID blocker tag, seen here embedded in a white mailing label
pasted onto the back of a pharmacy bag, would jam frequencies sent out from the
RFID tag on the bottle to protect the privacy of consumers. The RFID blocker tag was pasted to the back
of a pharmacy bag with a message from RSA Security explaining how the blocker
tag they developed works to protect consumers' privacy.
The blocker tag, which can be placed over a regular RFID
tag, prevents a receiver from scanning information transmitted by a tag by
sending the receiver more data than it can read -- the equivalent of a
denial-of-service attack. RSA doesn't have immediate plans to market the
blocker and is waiting to see whether industry widely adopts RFID technology.
APPENDIX B: useful quotations
relating to security systems
You got to be very careful if you don't know where
you're going, because you might not get there.
-- Yogi Berra
Woolsey-Swanson Rule:
People would rather live with a problem they cannot
solve rather than accept a solution they cannot understand.
The forest is safe because a lion lives therein and the
lion is safe because it lives in a forest. Likewise the friendship of persons
rests on mutual help.
-- Laukikanyay.
Software entities are more complex for their size than
perhaps any other human construct because no two parts are alike. If they are,
we make the two similar parts into a subroutine -- open or closed. In this respect, software systems differ
profoundly from computers, buildings, or automobiles, where repeated elements
abound.
-- Fred Brooks, Jr.
You see, I consider that a man's brain originally is
like a little empty attic, and you have to stock it with such furniture as you
choose. A fool takes in all the lumber of every sort he comes across, so that
the knowledge which might be useful to him gets crowded out, or at best is
jumbled up with a lot of other things, so that he has difficulty in laying his
hands upon it. Now the skilful workman
is very careful indeed as to what he takes into his brain-attic. He will have
nothing but the tools which may help him in doing his work, but of these he has
a large assortment, and all in the most perfect order.
It is a mistake to think that that little room has
elastic walls and can distend to any extent. Depend upon it there comes a time
when for every addition of knowledge you forget something that you knew before.
It is of the highest importance, therefore, not to have
useless facts elbowing out the useful ones.
-- Sir Arthur Conan Doyle, "A Study in
Scarlet"
If you are not for yourself, who will be for you?
If you are for yourself, then what are you?
If not now, when?
If science were explained to the average person in a way
that is accessible and exciting, there would be no room for pseudoscience. But
there is a kind of Gresham's Law by which in popular culture the bad science
drives out the good. And for this I think we have to blame, first, the
scientific community ourselves for not doing a better job of popularizing
science, and second, the media, which are in this respect almost uniformly
dreadful. Every newspaper in America has
a daily astrology column.
How many have even a weekly astronomy column?
And I believe it is also the fault of the educational
system. We do not teach how to think.
This is a very serious failure that may even, in a world rigged with 60,000
nuclear weapons, compromise the human future.
- Carl Sagan, The Burden Of Skepticism, The Skeptical
Inquirer, Vol. 12, Fall 87
I had a feeling once about mathematics -- that I saw it
all. Depth beyond depth was revealed to
me -- the Byss and the Abyss. I saw --
as one might see the transit of Venus or even the Lord Mayor's Show -- a
quantity passing through infinity and changing its sign from plus to minus. I
saw exactly why it happened and why tergiversation was inevitable -- but it was
after dinner and I let it go.
-- Winston
Churchill
"I wonder", he said to himself, "what's
in a book while it's closed. Oh, I know
it's full of letters printed on paper, but all the same, something must be
happening, because as soon as I open it, there's a whole story with people I
don't know yet and all kinds of adventures and battles."
-- Bastian B. Bux
It is not that polar co-ordinates are complicated, it is
simply that cartesian co-ordinates are simpler than they have a right to be.
-- Kleppner & Kolenhow, "An Introduction to
Mechanics"
Man is the best computer we can put aboard a
spacecraft... and the only one that can be mass produced with unskilled labor.
Wernher von Braun (1912 - 1977)
Crash programs fail because they are based on the theory
that, with nine women pregnant, you can get a baby a month.
Wernher Von Braun (1912 - 1977)
Of all men's miseries, the bitterest is this: to know so
much and have control over nothing.
-- Herodotus
APPENDIX C
more about retina scanning
Retina scanning is hindered by cataracts and
glaucoma. Citing
www.hearthstonedesigns.com/retina-scan-technology.htm
|
... maps the capillary pattern of the retina, a thin
(1/50th inch) nerve on the back of the as cataracts and glaucoma can render a
person unable to use retina scan technology, as the blood vessels can be
obscured. IBG concerns have slowed the
development of such technology, but investors apparently expect that to
change: |
Citing http://www.rjagroup.com/sako/security_corner/harizan_STD_0902.htm
SECURITY CORNER
BIOMETRICS: ADVANTAGES AND APPLICATIONS
By: Robert J. Harazin, CPP
This article appeared in the September 2002 issue of
Security Technology & Design
"There is no single best biometric technology, but
the requirements of a specific application determine which biometric system is
best."
In today's world of increased security awareness and
access control, everyone is looking for improvements in technology. There are
three different authentication methods used in security today.
The first relies on something you know, like a password
or PIN. The second relies on something
you have, like a card key, smart card or token. The last type of authentication
relies on what you are-this type is biometric authentication. Biometrics is based
on the measurement of physiological or behavioral characteristics to determine
or verify identity.
Of these types, biometrics is the system that can afford
the greatest degree of security.
Passwords and PINs can be guessed, lost or even shared, tokens can be
stolen, but biometric data cannot. These systems provide other advantages over
traditional card systems, including elimination of buddy punching timeclock and
deterrence of fraud attempts.
Currently there are two primary uses for a biometric
system: physical access and logical access. Physical access systems monitor,
restrict or grant the rights to a user for movement into or out of an
area. When used in physical access
systems, biometrics generally replaces or is used in conjunction with keys, access
cards, PINs and security guards. Logical
access systems monitor, restrict or grant access to data or information. Uses of logical access systems include
logging onto a PC, accessing data from a network or authenticating a
transaction. The basic biometric function of acquiring and comparing data is
often identical between physical and logical access systems.
In our everyday lives, we are accustomed to recognizing
friends' and co-workers' faces and voices. In a biometric system the actual
matching function is much more complex.
The first thing a user must do to be able to use a biometric system is
to present his or her biometric data. This step is called the enrollment
process. Biometric data is acquired and
processed and then stored on what is called an enrollment template, which is
kept in the system.
When a user presents his or her biometric data to the
system for verification, another template is created, called a match template.
The data on the match template is then compared to the data on the enrollment
template.
A score is created for the comparison of the two
templates, and this score is then compared against a threshold-a predefined
number that establishes the score required for a match to occur. The system will then grant access, refuse access
or request another sample, depending upon the results of the comparison. There
are several biometric technologies available today, each with its own strengths
and weaknesses. There is no single best
biometric technology, but the requirements of a specific application determine
which biometric system is best. The following graph shows some of the strengths
and weaknesses of the leading biometric technologies available today.
Biometric Technologies | Ease of Use | Accuracy | User
Acceptance | Required Security Level |
Long-Term
Stability | Error Incidence
Signature |
High | High | Medium | Medium | Medium | Changing Signatures
Voice |
High | High | Medium | Medium | Medium | Colds, Noise, Weather
Fingerprints |
High | High | Medium | High | High
| Age, Dirt, Dryness
Hand Geometry | High
| High | Medium | Medium | Medium | Age, Hand, Injury
Retina |
Low | Very High | Medium | High | High
| Glasses
Iris |
Medium | Very High | Medium | Very High | High
| Poor Lighting
Face |
Medium | High | Medium | Medium | Medium | Age, Glasses, Hair
Signature Scan
The signature scan technology uses several aspects of an
individual's signature to verify his or her identity. This technology measures
the physical activity of the person signing and looks at the behavioral
components of the signature, such as the stroke, speed and pressure of the
individual's hand. Someone could learn to sign a person's signature so it is visibly
identical to the real thing, but because this system operates using behavioral
rather than physiological characteristics, it is difficult for an imposter to
fool the signature scan system.
Voice Scan
Another biometric technology that is in use today is the
voice scan system. A user of this
technology must speak a particular word or phrase to have his or her identity
verified. Voice scans combine behavioral and physiological biometrics by using
distinctive aspects of the voice-what is said and how it is spoken. The voice scan system is text-dependent,
meaning that a user must speak a particular phrase or word to be recognized.
This system will not verify the voice of someone speaking random words or
phrases that have not been entered into the system as a template. Most
individuals will find this technology easy to use, but the error rate for
identification could be high if the person has a cold or if environmental
conditions around the reader distort or muffle the voice.
Fingerprint Scan
Fingerprint scan technology is the most commonly used
biometric technology to identify or verify the identity of individuals. This
type of system has made many technological advancements and is capable of a
high degree of accuracy. The acquisition
of a high-quality image of the fingerprint is the first challenge
for a finger scan system. This is a major problem
because fingerprint quality can vary from person to person and from finger to
finger. The fingerprint comprises ridges
and valleys that form distinctive patterns, such as swirls, loops and arches.
Fingerprint ridges and valleys are characterized by
discontinuities and irregularities known as minutiae. Minutiae are the
distinctive features on which most fingerprint technology is based. An
alternative technology is based on pattern matching.
Pattern matching verifies identity by examining a series
of ridges as opposed to discrete points. The use of multiple ridges reduces the
dependence on minutiae points, which are affected by wear and tear.
Finger scan technology is a strong solution for a range
of environments. It will likely continue
to grow in use with logical and physical access applications, and will likely
be central to the biometric industry's growth.
Hand Geometry Scan
Hand scan technology utilizes distinctive aspects of the
height and width of the hand and fingers. This technology has been in use for
many years and is mainly used for physical access and time and attendance
applications.
To use this scan, an individual places his or her right
hand on a metal surface with the fingers slightly separated and the palm
resting flat. Some units require the
user to enter a PIN as well. Hand scan
devices are generally constructed out of metal and plastic and have few easily
damaged components. These units are designed to be located in any type of
environment, even where other biometric devices would be inoperable. They will operate through temperature and
moisture extremes, and will read even if the user is wearing thin latex
gloves. Because physical access devices
are more likely to be exposed to the elements, this represents a major
advantage for hand scan technology.
Retina Scan
Retina scan is perhaps the most accurate and reliable
biometric technology. It is also among
the most difficult to use and is perceived as intrusive. The retina is the surface on the back of the
eye that processes light entering
through the pupil. Retina scan is usually used for access control where a high
degree of security and accountability is required.
The operation of this device requires that the user
place his or her eye very close to the unit's embedded lens. Beneath the lens is the imaging component,
which consists of a small green light against a white background. The user watches this light, and, when
triggered, the light moves in a circle, measuring the retinal patterns through
the pupil. The user must remain perfectly still during this process, because
any movement will compromise the image acquisition process. The retina contains at least as much
individual data as a fingerprint, and it is less susceptible to intentional and
unintentional modification. However,
certain eye conditions and diseases such as cataracts and glaucoma can render a
person unable to use retina scan technology, as the blood vessels can be
obscured.
Two things detract from the retina scan's widespread
use. First, people feel that the eye is
a delicate area, so many are hesitant to use the device. Second, the cost per device puts it on the
expensive end of the physical security spectrum.
Iris Scan
Traditionally used only in high-security access control
applications, iris scan technology has now been introduced to the airline
industry, prisons and the banking industry for use in ATMs. The iris scan
process requires the acquisition of a high-resolution image of the eye by an
infrared imager in order to effectively map the details of the iris. Because the distinctive features of the iris
differ substantially from user to user, testing has shown the iris scan to be
extremely resistant to false matching.
Iris scan technology is a tremendously accurate biometric.
Face Scan
The human face has distinctive features that can be used
to verify or identify individuals. The
features that are most often utilized are the upper ridges of the eye sockets,
the areas around the cheekbones, sides of the mouth, shape of the nose and the
position of major features relative to each other. These features are used
because they are least likely to change over time. Facial scan systems can be
used in conjunction with ID card systems, booking stations and for various
types of surveillance operations. The most successful implementations of these
systems take place in environments where cameras and imaging systems are
already present.
The process begins with the image acquisition through a
high-resolution camera. Securing a
quality image can be a problem if the subject is standing to far from the
camera, the lighting changes or if the subject is at an angle to the camera. A new and developing area for facial scan is
in the area of surveillance. Biometric
surveillance systems are currently being used in major gambling casinos and in
a few police applications. Of these two applications, casino usage is more
widespread and less controversial. But in the public areas where law
enforcement has tried to pick out possible criminals, the use of facial scan
has proven to be very controversial because of the high number
misidentifications. The major problem here is the enrollment factor. Law enforcement for the most part is loading
its systems with pictures of wanted criminals from mug shots or pictures of
very low quality. Another factor is that
the wearing of hats, glasses, facial hair and hairstyles can affect the
verification process. Facial scan technology in a closed environment with good
enrollment procedures can afford good security and protection.
Some biometric devices are user friendly, while other
types require a greater amount of training on the proper way for the user to
present biometric information. For example,
placing your finger or hand on a reader is relatively simple, but the aligning
of the head with a device for use with a retina, iris or facial scan can at
times be difficult. As technology develops, the use of these devices will
become easier and less intrusive.
Biometrics may offer increased security, increased
convenience or enhanced services. In
some applications, the biometric system serves only as a deterrent, while in
others it is central to the security system operation. Regardless of the reason for using
biometrics, there are two common elements that come into play with its use:
1. The
high degree of certainty regarding the verification of an individual's identity
and
2. The
benefits that lead directly or indirectly to cost savings or to reduced risk of
financial losses for an individual or institution.
Some biometric systems can be very costly, but sometimes
price cannot outweigh the need for high security and protection.
This article appears permission by Cygnus Business
Media, Inc
appendix D
RFID references:
RFID uses and abuses are often discussed in the
comp.risks digest.
http://www.google.com/search?hl=en&ie=ISO-8859-1&q=rfid+jackson
leads to Good RFID commentary
http://home.att.net/~randall.j.jackson/rfid.htm
http://home.att.net/~randall.j.jackson/pet-chip.htm
Microchips and Your Pet
What You Should Know Before Microchiping Your Pet
http://home.att.net/~randall.j.jackson/rfidnews.htm
Recent Industry News
http://www.prisonplanet.com/022904rfidtagsexplode.html
http://portland.indymedia.org/en/2004/03/281760.shtml
RFID Tags in New US Notes Explode When You Try to
Microwave Them [I suspect it's just a metal thread]
We could have left it at that, but we have also paid
attention to the European Union and the 'rfid' tracking devices placed in their
money, and the blatant bragging of Walmart and many corporations of using
'rfid' electronics on every marketable item by the year 2005.
http://www.eetimes.com/story/OEG20011219S0016
Euro bank notes to embed RFID chips by 2005
By Junko Yoshida
EE Times December 19, 2001
SAN MATEO, Calif. - The European Central Bank is working
with technology partners on a hush-hush project to embed radio frequency
identification tags into the very fibers of euro bank notes by 2005, EE Times
has learned. Intended to foil
counterfeiters, the project is developing as Europe prepares for a massive
changeover to the euro, and would create an instant mass market for RFID chips,
which have long sought profitable application.
http://www.stargeek.com/item/62823.html
EPCglobal sets up RFID product code management system
APPENDIX E
more about SmartCard systems
Laptop computers are vulnerable to theft or casual
tampering because most assume a single user.
Passwords and account locks are barely useful because the hard drive is
so easily removeable (usually in an enclosure that facilitates removal), or
external storage media are used (USB interfaced hard drives, CDs, floppies,
solid state storage).
SmartCards or USB interfaced cryptographic devices are an
effective solution because they encrypt the data on the disk drive as well as
authenticate the user.
Most systems offer Key Escrow systems for recovering the
disk data even if the SmartCard is lost or stolen.
The IBM Smart Card Security Kit claims:
|
The IBM Smart Card Security Kit is an integrated
hardware and software SecureWay soluion. It provides advanced security
features for desktop computers that includes Transparent Data Encryption,
Multi-User access, Digital signature for both Netscape and Microsoft Internet
Explorer and is also Security Dynamics "SoftID" ready. ·
Protects against information theft ·
Protects again unauthorized use of your
computer ·
Provides file encryption and decryption ·
Easy transfer of self decrypting documents ·
Instant Secure Screensaver ·
Supports many widely used security applications |
A.
Self
Contained Credentials
[risks_23_35]
RISKS-LIST: Risks-Forum Digest Tuesday 4 May 2004 Volume 23 : Issue 35
FORUM ON RISKS TO THE PUBLIC IN COMPUTERS AND RELATED
SYSTEMS (comp.risks)
ACM Committee on Computers and Public Policy, Peter G.
Neumann, moderator
A recent edition of the Risks digest [risks_23_35]
reviewed the book "Non-Repudiation in Electronic Commerce", Jianying
Zhou, 2001, 1-58053-247-0
This relates to Jerry Chen's presentation of
Non-repudiation Secure File Transfer where a method for secure, authenticated
offline file transfer was presented.
Machine-readable id cards could benefit from that as well.
Most conversations start with exchanging identity and
agreeing on how to proceed with the conversation (session key, encryption
method, etc) and cannot proceed until each reply is received.
Analogously, most machine-readable ID systems require a
real-time response from a central server to verify the id-number and verify if
the person has permission for the action.
For example:
I swipe my magnetically encoded ID card at the front
door. The card reader sends to the
central server "I am card #634592346"
The central server may reply
1. "yes,
unlock the door and let him in"
2. "buzz
and reject the card, it is no longer valid"
3. "buzz
and reject the card, it's the wrong time for him to enter"
The hand biometric reader may control a door too, and
the protocol proceeds as follow:
1. I
enter my ID on the keypad, or swipe the ID card scanner to central server
"employee 42 is at the door"
2. server
to scanner "let him prove it"
3. I
place my hand in the scanner and the readings are sent to the server
4.
the central server may reply
"yes, unlock the door and
let him in because the hand matches the profile in the database"
All these systems fail if communication to the server is
lost, or the server fails to respond.
Consider the way stores process credit cards. Most use a terminal to a server that quickly
validates if the card is valid and initiates a financial transaction. But if the server is unavailable, the backup
system it to look up the credit card number in a book of invalid numbers and
take an imprint of the card to prove it was physically present. This system fails to detect cards invalidated
after the list was printed but it's mostly reliable and trusted.
Authentication can benefit from the techniques used for
delayed transmission when a central server is not available. Machine readable devices such as SmartCards
or high density barcodes may contain their own certificates, or an entire
message describing the bearer's credentials.
A server is needed only to assure none of the certificates were revoked
and the card's not stolen.
It could work like this: NJIT generates a list of
credentials for me (what buildings I may access, what facilities I may use,
etc.) encrypts it and makes an electronic "envelope" for it. I may store it on any medium (SmartCard,
floppy, CD). When I want access to something participating in the security
system, I present my credential. Just like the offline reading of the secure
email, the credentials are unwrapped and validated. A server is needed only for checking the
revocation list. If the server is not
available, there is sufficient trust that the access may be granted.
I cannot alter or tamper with my credentials because I
lack NJIT's private key so I cannot create a proper signature.
Appendix F
Subway fare systems
The NY subway system originally used metal coin-like
tokens for the fare payment system.
Slugs (fake tokens) circumvented fare payment because it's easy to fool
the mechanical-only turnstile mechanism.
Then the token design was changed to use 2 dissimilar metals, only to
find that identical tokens were used in other states and they cost
significantly less!
Now the all electronic "Metrocard" fare card
system has totally replaced tokens. But
there's a new way to circumvent fare payment: bending the card gives free rides
http://www.gothamist.com/archives/2003/08/24/bending_your_metrocard.php
Bending Your Metrocard
The Times looks at how Metrocards aren't safe from
thieves trying to steal fares, specifically with techniques like "bending
the card" which is a far cry from ancient techniques of stealing
tokens. The MTA estimates they lose
$260,000 a year on card-benders, versus $5 million on turnstile jumpers. The
Morning News coined a brilliant Metrocard phrase: Metrotard - A person in front
of you at the subway turnstile who cant figure out how to swipe his or her
subway pass. Maybe they were simply fare
swiping. Oh, and the Times piece answers
what's done with the discarded Metrocards that litter stations: Absolutely
nothing.
Posted by Jen Chung in News: NYC
how to "bend" a metrocard
·
bend the back middle between the C and the A in
the word CARD.
·
Bend right in the center in the black strip.
·
Swipe in the turnstiles 3 times. the forth time
you should get through if done right.
Citing http://www.yellowratbastard.com/Metrocard/Metrocard.asp
How To Manipulate Metrocards
"Getting over" has been a time honored
tradition in this city, passed down from one generation to the next. From
booster bags to jamming payphones there always seems to be a way around
everything.
My personal favorite was finding a way around
turnstiles, or over them. A petty crime that allowed me, as a kid, to turn this
city into a playground not to mention saving a couple of bucks. That changed
when the city's crackdown on fare beating really cramped a lot of people's
style. But as I said, there always seems
to be a way around everything. The following is a trick of the trade "How
To" if you will, from the usual suspects. It might take a few tries to get
it, so take your time and be on point. Once you get it, you'll thank me. First of all you're going to need old
Metrocards. Only full fare cards can be
used. Every station is equipped with a
machine that tells you the status of the card.
$) Now comes the tricky part. Bending the card
correctly. Along the bottom of the card
it says "Insert this way/this side facing you." The G spot is the backslash. Holding the card
facing you with your index fingers on the back of the card, bend it slightly
along the backslash. Make sure that the
crease doesn't go further than halfway up the black strip. This step is key, so
be precise.
$$) Now for your first swipe. If the card was bent
correctly, the screen on the turnstile should display, "please swipe
again." Do as it asks. After the
second swipe the screen should display, "please swipe again at this
turnstile." If it doesn't, keep
swiping until it does.
You can try unbending and re-bending the card to achieve
the desired result.
$$$) Now, unbend your card and swipe a third time. This
swipe should be the ticket. The
turnstile should been you through as if you had a buck fifty left on the
card. If it doesn't, swipe it a fourth
time and that should do the trick.
DISCLAIMER: All this is, is the Metrocard system
allowing you through in case you really do have a fucked up card. It's not an exact science so don't be
surprised if you have to try things a little differently than I've described them. You only get one fare per card so it's not an
end all be all for your transportation woes. This is illegal and should be
treated accordingly. I don't suggest
attempting this in Times Square or at any busy station unless you're a
pro. Come to think of it, I don't
suggest anyone doing this. Good luck.
http://www.nycartcollective.com/blog/archives/cat_mta_reboot.html
Another new failure mode for the NY Subway System: Metrocard
vending machine BSOD: Win NT.
The Chicago subway has a wireless fare card only for
monthly passes. This sounds similar to the EZ Pass system: account status is
available online and the account is linked to a credit card for auto-deduction.
http://www.chicago-card.com/ccplus/faq.aspx
http://www.chicago-card.com/ccplus/faq.aspx
How and where can I use my Chicago Card Plus? To board a bus or enter through a rail
station turnstile, simply touch your Chicago Card Plus to the touchpad on the
front of rail station turnstiles and bus fareboxes on all CTA and Pace buses. Chicago Card Plus is accepted for full fare
payment on all CTA rail and bus routes, and Pace buses (except Pace route
#835). Metra does not accept CTA fare
media.
Will my RTA Reduced Fare Permit SmartCard change to
Chicago Card Plus? No, this program will
not affect your reduced fare SmartCard.
You will continue to use the same card.
What will the bus farebox and rail station turnstile
displays read when I use my Chicago Card Plus?
Your choice of Pay-Per-Use or 30-Day Passes may not be
accurately reflected on bus farebox and rail station turnstile displays but
will be accurately reflected in your account. Your balance will never be
displayed on turnstiles or fareboxes because your balance is held in an account
and not on your card.
References on the CD
[jonas03]
Jonas, Jeffrey
Balancing Privacy and Trust With A Smart Card Based
National Identity Card
paper presented for NJIT's CIS786 Pervasive Computing
Summer 2003, unpublished.
[jonas03a]
Jonas, Jeffrey
Introduction to Smart Cards
paper presented for NJIT's CIS786 Pervasive Computing
Summer 2003, unpublished.
[jonas03b]
Jonas, Jeffrey
Introduction to WiFi
paper presented for NJIT's CIS786 Pervasive Computing
Summer 2003, unpublished.
[jonas03c]
Jonas, Jeffrey
Introduction to DMCA (Digital Millennium Copyright Act)
and DRM (Digital Rights Management)
paper presented for NJIT's CIS786 Pervasive Computing
Summer 2003, unpublished.
[lutz03]
Lutz, Robert
Augmented Reality, paper presented for NJIT's CIS786 Pervasive Computing
Summer 2003, unpublished.
[RISKS]
FORUM ON RISKS TO THE PUBLIC IN COMPUTERS AND RELATED
SYSTEMS (comp.risks)
ACM Committee on Computers and Public Policy, Peter G.
Neumann, moderator
mirrored at
http://catless.ncl.ac.uk/Risks/23.19.html
http://www.csl.sri.com/users/risko/risks.txt
references NOT on the CD
[HILTZ03]
Hiltz S.R., Han H., Briller V., 2003,
Public Attitudes towards a National Identity "Smart
Card:"
Privacy and Security Concerns Proceedings of the Hawaii
International Conference on System Sciences (HICSS), 2003.
[SCHN96]
Schneir, B.
Applied Cryptography Second Edition
New York: Wiley, 1996.
[SCHN03]
Schneir, B.
Beyond Fear: thinking sensibly about security in an
uncertain world
New York: Copernicus Books, 2003.
[SCHN04]
Schneir, B.
Crypto-Gram is a free monthly e-mail newsletter on
computer security and cryptography from Bruce Schneier
http://www.counterpane.com/crypto-gram.html
[rfc3457]
Requirements for IPsec Remote Access Scenarios
http://www.faqs.org/rfcs/rfc3457.html
[rfc3193]
RFC 3193 - Securing L2TP using IPsec
http://www.faqs.org/rfcs/rfc3193.html
[rfc1824]
RFC 1824 - The Exponential Security System TESS: An
Identity-Based Cryptographic Protocol for Authenticated Key-Exchange
(E.I.S.S.-Report 1995/4)
http://www.faqs.org/rfcs/rfc1824.html
[rfc1875]
RFC 1875 - UNINETT PCA Policy Statements
http://www.faqs.org/rfcs/rfc1875.html
[GSA]
U.S. General Services Administration Smart Card
Initiative
[GSA04]
Survey of Federal Smart Card Projects
February 2, 2004
http://www.estrategy.gov/scripts/sc_viewera.asp
[SCHNE03]
Bruce Schneier.
Beyond Fear. Copernicus Books,
2003
[CRYPTO]
Crypto-Gram: a monthly newsletter on security
[Utah]
http://www.mudcat.org/kids/@displaysong.cfm?SongID=4670
http://sniff.numachi.com/~rickheit/dtrad/pages/tiPHOEBESN;ttPHOEBESN.html
[HOMEL]
Understanding the Homeland Security Advisory System
http://www.dhs.gov/dhspublic/display?theme=29
other recommended reading
http://developer.netscape.com/tech/security/basics/index.html
How SSL Works
Makes security products most notably they are the top level
Certificate Authority
A major source of security software and devices such as
SecurId tokens
To learn more about phrenology:
http://future.newsday.com/5/fbak0528.htm
The Museum of Questionable Medical Devices in
Minneapolis has one of the few remaining working models of a complicated
mechanical phrenology device, the Psycograph, that made its big splash at the
Chicago World's Fair in 1933. The hat-like device was placed on a person's head
and provided a mechanical skull reading.
Museum of Questionable Medical Devices
http://www.mtn.org/quack/devices/psycogrf.htm
http://www.mtn.org/quack/devices/psychist.htm
Lists many other Phrenology web sites.